Digital technology has a significant impact on how we live and work. We take this digital life for granted as we move fluidly between different devices, networks, clouds, etc., at work and home. We share sensitive data with a few clicks, and its constant flow creates a complex interdependency that heightens risk. Multiple threats are passed along as a chain reaction or contagion with incredible speed and catastrophic results. What are the 5 types of cyber risk?
It would be relatively easy to put together a top ten cyber security threats list or to project into the future and extend that list to fifteen or more. But to talk about cyber risk in an actionable and relatable way to a business owner, we don’t have to go that far. We can address a smaller subset of problems, and we will be several steps ahead of the pack. When we look at the top five cyber risks, we’re talking about significant issues, expanding threats that make headlines for big businesses, and headaches for organizations of all sizes.
As you evaluate this environment and understand the scale and scope of the risk, it can be intimidating. Slicing it up into smaller pieces can make it manageable. Let’s talk about the top 5 cyber risks, some of the causes or “gateways” making them more prevalent, and the solutions that attack these threats head-on.
- Social Engineering – these dirty tricks have a reputation of being easy to spot or simple-minded, but that does not align with reality. Whether it’s the official-looking email scam, the office gift card scam, or other newer versions of these “classics,” social engineering scams are increasing in sophistication, success, and prevalence. A few types of social engineering attacks include phishing, baiting, tailgating, whaling, quid pro quo, scareware, and BEC. Do not let the cute names fool you!
- Third-Party Exposure – companies use third parties for all services, such as payment processing. These companies will handle your company’s sensitive data or that of your company’s customers. If their data security is compromised, your company can still be liable for the impact of that breach.
- Patch Management – Vulnerabilities can be exploited when hardware or software is outdated and security updates haven’t occurred in a timely fashion. Hardware or software obsolescence can creep up on you. If you cannot make security updates, you might have a problem with outdated resources. If security updates can be made but are not automatic, human intervention is required.
- Cloud Vulnerabilities – Cloud services are vulnerable to many attacks, including hijacking and denial of service attacks. Attackers are not only targeting platforms like AWS, Microsoft Azure, and Google Cloud but also organizations within the cloud.
- Ransomware – In 2021, the FBI reported 649 complaints from critical infrastructure organizations related to ransomware. The healthcare and financial sectors are the hardest hit by ransomware attacks.
It’s easy to think of cyber security as something purchased and switched on. While digital tools are a component, it’s crucial to acknowledge the human factors involved. A Stanford study revealed that nearly 90% of security breaches were the result of human error. That means, you can pick almost any category of cyber security, and human error is going to play a role. Delegating the work to a siloed department or mechanical fix is not a strategy. Broad, holistic employee training must be a component in preventing cybercrime. Training might begin with understanding what makes cyber risk so prevalent.
What Makes Cyber Risk So Common?
The interdependence, size, scale, and ubiquity of our digital presence are among the contributors to an environment that makes cyber risk ever-present for organizations of all sizes. A glossary of digital factors imposing on our daily home and work lives and creating an environment open to risk will include:
The Internet of Things (IoT) – gadgets and devices that store, send and receive data have rushed into our homes and workplaces. Not all of them are perfected or secure. They are a source of a continual flow of data and digital interactions and are vulnerable to attack or failure.
Bring Your Own Device (BYOD) – The global market for BYOD and enterprise mobility soared during the pandemic. Experts estimate the market at $84BB in 2022. For better or worse, the expectation for many professionals is to be able to work from anywhere, at any time, on any device. The trick is to balance benefits with vulnerabilities.
Multicloud Environment: Is your data confidential? As operations move to not just one cloud but multiple cloud environments, the threats to data integrity increase.
Risk concentration – consider the ubiquity of Amazon or Amazon Web Services. If there were a successful attack on their infrastructure, the ramifications would be far-reaching.
Opacity – the proprietary nature of digital technology means we all have to work even harder to understand the systemic relationships between private technology and end-users.
Scale – As the authors of a Carnegie Endowment cybersecurity report note, the vastness of our interconnected digital environment creates “low marginal costs for high-impact attacks.”
Intelligent Opponents: Intelligent adversaries act with patience and savvy to find cyber vulnerabilities.
Make Cybersecurity More Manageable
The omnipresence of technology in our personal and work environment and the exponential growth of cyber security threats can make it feel like trying to catch a boulder rolling down a hill. An IT consultant can add perspective and support.
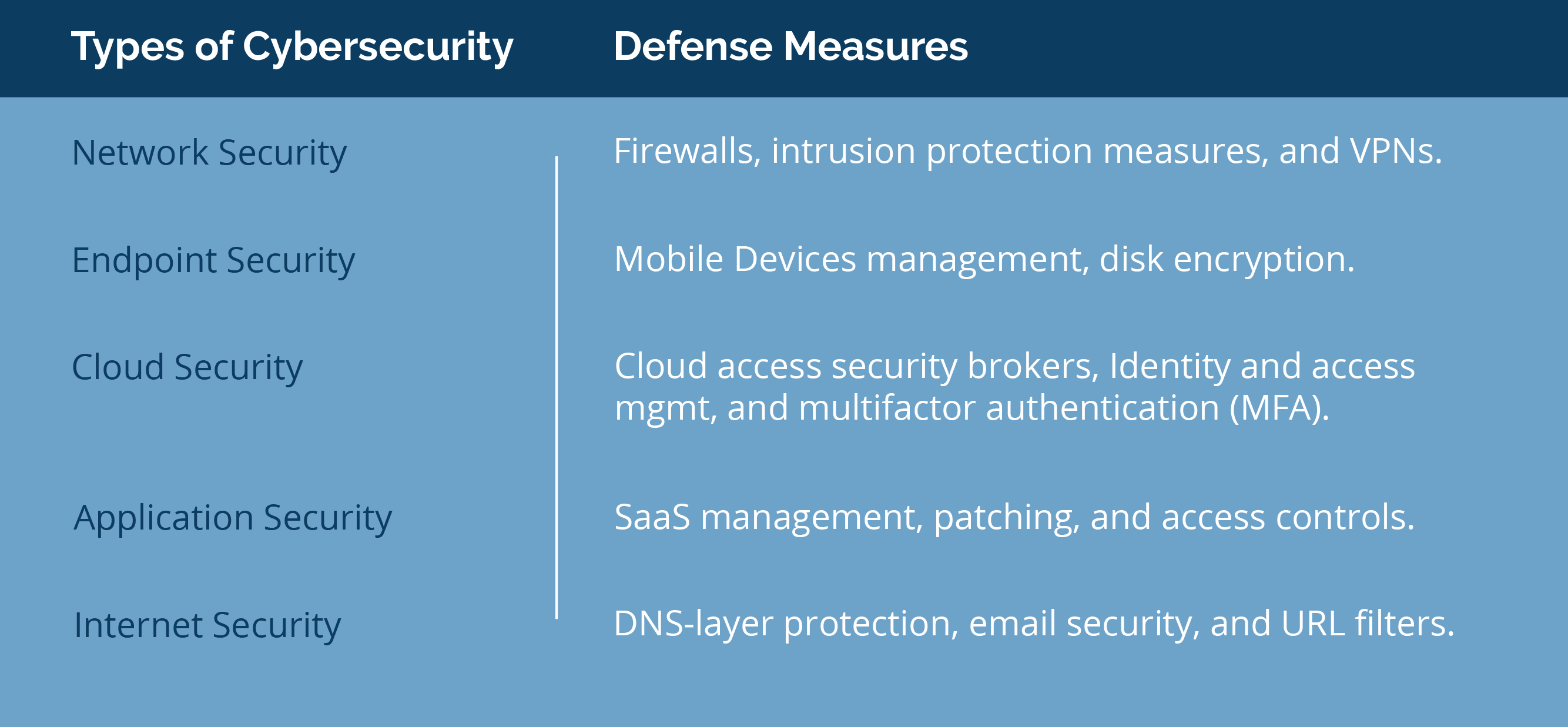
It’s helpful to break down cybersecurity into its relatable and easily understood components. Publicly-traded cyber consultant Sailpoint, citing the National Institute of Standards and Technology (NIST), offers a simple definition of cybersecurity: “the ability to protect or defend the use of cyberspace from cyberattacks.” Sailpoint breaks cybersecurity down further into five categories.
- Network security – the broad infrastructure like routers, servers, and data centers
- Endpoint security – the personal and corporate devices used to access network assets
- Cloud security – the public, private, or hybrid cloud options
- Application security – the applications, including cloud-based applications
- Internet security – securing the internet, email and related layers of data transfer
The breakdown of cybersecurity types, with defense measures for each are shown below.
You might need help in identifying which threats apply to your organization. A step you can take is to assess your cyber security risk. The following checklist, adapted from Tech Target, gives you a starting point:
- Scope. Determine the extent of the risk assessment. This could include limiting your initial evaluation to a manageable business unit or set of applications. You’ll need participation and buy-in from colleagues. Build a diagram or illustration to make the risk easier to understand and comprehend.
- Identify. Identify assets and cybersecurity threats. Build a “threat library” and be systematic in your approach by first identifying the dangers and what could go wrong, then outlining the vulnerabilities, the assets affected, and the consequences of each scenario.
- Analyze and Rate. Analyze risks and determine potential impact. Rate the likelihood of a risk and its effects to illustrate the real-world implications.
- Prioritize. With likelihood and impact mapped out on a matrix, you can attach a figure to the risks and prioritize. Classify risks as “avoid,” “transfer,” or “mitigate.” There is always risk left over, but these strategies can help manage the manageable.
- Document. Take the time to document all the identified risks. Name them, date them, note the controls, and determine who owns the risk. Next, set a cycle for revisiting this list and updating it as new threats arise or others fall away.
You might start small, focusing on one facet of your business. Try, for instance, focusing your cyber risk assessment on a department that places a heavy demand on your IT infrastructure. The work of this one department can establish a template for putting cyber security controls in place across departments. It can also ensure that some of your ‘power users’ are at the table to help set the company standards for cyber security controls.
Get Support
What are the 5 types of cyber risks for your organization? Do you identify with those we’ve outlined here? Even an organization with substantial IT resources can use an assist when it’s time to assess risk and create a plan for directing cyber security resources in the most effective manner possible. An IT consultant can be that extra resource that drives a special initiative forward with the least disruption to your everyday operations. Contact eMPiGO today to talk to an expert.
