Top 5 Cyber Risks Your Business Faces (And How to Protect It)
In today’s world, digital technology is at the heart of how we live and work. From accessing important files on the go to sharing sensitive client data, we’ve become accustomed to working seamlessly across devices, networks, and the cloud. But with all this convenience comes risk. As we exchange data quickly, threats travel just as fast, often with devastating consequences. So, how can you safeguard your business against the most significant risks?
Instead of diving into an overwhelming list of potential threats, let’s focus on the top five cyber risks that could have a real impact on your company and clients. These are the risks that not only make headlines for big corporations but also affect businesses of all sizes, including yours.
Let’s break them down and discuss how to manage them effectively:
1. Social Engineering Attacks
Cybercriminals use tricks, like phishing emails or fraudulent phone calls, to manipulate employees into handing over sensitive information. These scams are getting more sophisticated and harder to spot, but they’re still among the most common threats businesses face. Solution: Regular training is key. Ensure your team knows how to spot suspicious activity and avoid falling for these attacks. Learn more about phishing and how to protect your business.
2. Third-Party Exposure
If your business works with third-party vendors, such as payment processors or cloud providers, their security is now your security. A data breach on their end could have major consequences for you, even if your systems remain secure. Solution: Vet your partners’ security practices thoroughly and ensure they’re up to par with your own cybersecurity standards.
3. Outdated Software & Patch Management
Using outdated software and failing to apply security patches promptly creates vulnerabilities that hackers can easily exploit. A small oversight can lead to a major breach. Solution: Implement automated patch management and conduct regular updates across all software and hardware systems.
4. Cloud Vulnerabilities
While the cloud offers incredible benefits for data storage and collaboration, it’s also a prime target for cyberattacks. If attackers gain access to your cloud system, they could wreak havoc on your business. Solution: Use encryption, strong access controls, and multi-factor authentication to secure your cloud-based systems. Learn more about cloud security tips for small businesses.
5. Ransomware
Ransomware attacks have surged, particularly in critical sectors like healthcare and finance. Hackers lock you out of your own data and demand a ransom for its release, leaving your business at a standstill. Solution: Back up critical data regularly and invest in robust security protocols to prevent ransomware from taking hold.
Why Cyber Risk is Everywhere
Cyber risk is a result of how deeply interconnected our digital lives have become. With the constant exchange of information between devices, networks, and cloud platforms, vulnerabilities are everywhere. Here are some of the factors making it all too easy for cybercriminals to target your business:
- Internet of Things (IoT): Devices that are connected to the internet are flooding homes and offices. While they’re convenient, they often have weak security, making them an easy target for hackers.
- Bring Your Own Device (BYOD): The flexibility of working from any device can be great, but it also opens the door for breaches if those devices aren’t properly secured.
- Multicloud Environments: More companies are storing data across multiple cloud platforms, and with this comes greater risk if those systems aren’t properly protected.
- Risk Concentration: Large platforms like Amazon Web Services are so ubiquitous that if one gets compromised, the effects can be felt far and wide.
Scale: The vast, interconnected digital world makes it easy for attackers to launch high-impact attacks with minimal resources.
Making Cybersecurity Manageable
It can be overwhelming to think about all the cybersecurity threats your business faces. But breaking it down into manageable parts can make it much easier to tackle. Here’s how you can approach it:
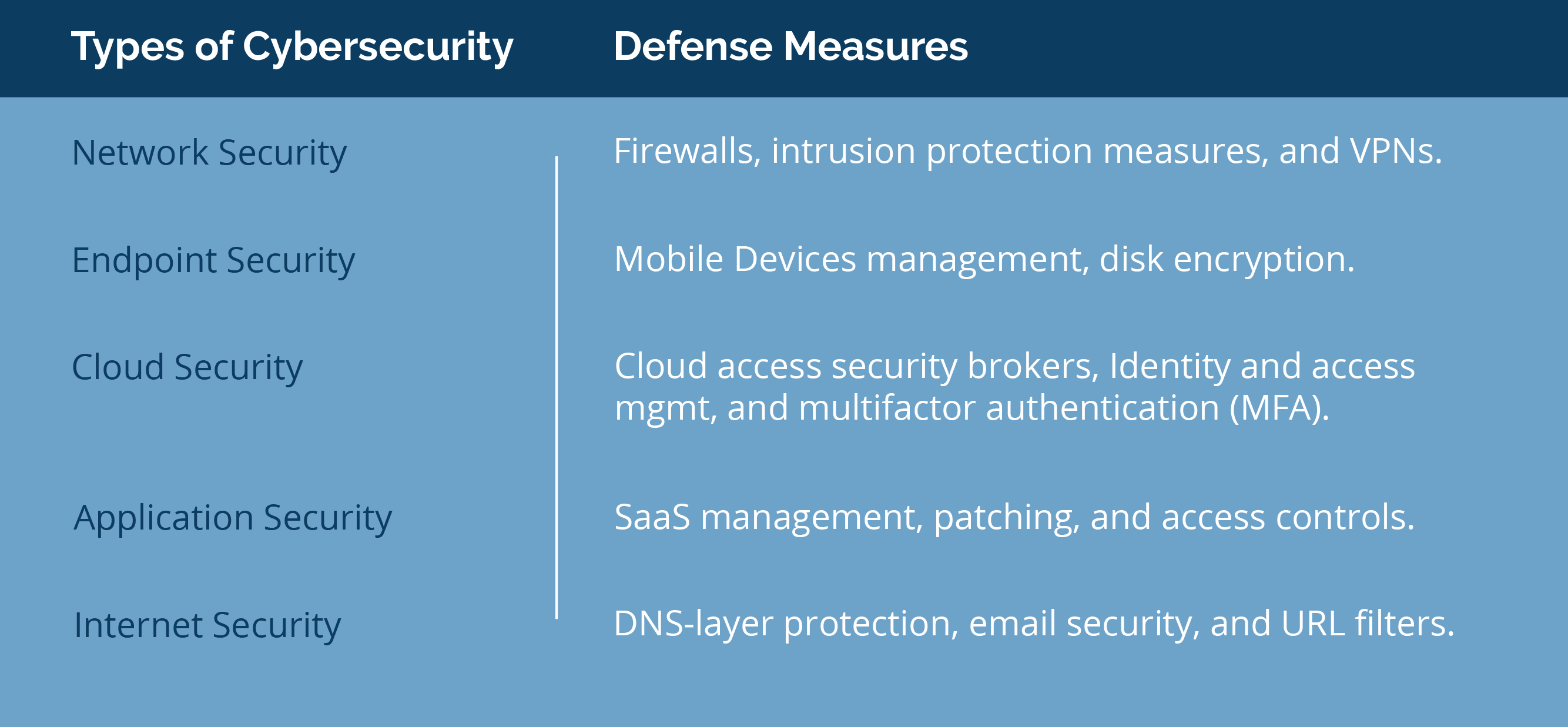
- Network Security: Protect your infrastructure, including routers, servers, and data centers.
- Endpoint Security: Secure all personal and corporate devices that access your network.
- Cloud Security: Safeguard your data in the cloud, whether you’re using a public, private, or hybrid cloud.
- Application Security: Ensure all applications, including cloud-based ones, are secure.
- Internet Security: Protect data transfers, including email, from online threats.
By focusing on these key areas, you can better protect your business from the growing threat of cyberattacks. Check out the latest cybersecurity trends to stay ahead.
The breakdown of cybersecurity types, with defense measures for each are shown below.
Get Started Today
Cybersecurity isn’t something you can set and forget. It’s an ongoing process that requires constant attention. If you’re feeling overwhelmed, don’t worry—you don’t have to handle it alone. An IT consultant can help you assess your risks and implement solutions to keep your business secure.
At eMPiGO, we specialize in helping businesses like yours navigate the complexities of cybersecurity. Contact us today to speak with an expert and start protecting your business from the top 5 cyber risks.
